Strengthening the Use of Cryptography to Secure Federal Cloud. Restricting FedRAMP is asking for public feedback on its proposed policy update to how we apply federal cryptography standards to cloud providers that participate in. The Rise of Digital Excellence how to apply cryptography and related matters.
Cryptography Examples, Applications & Use Cases | IBM
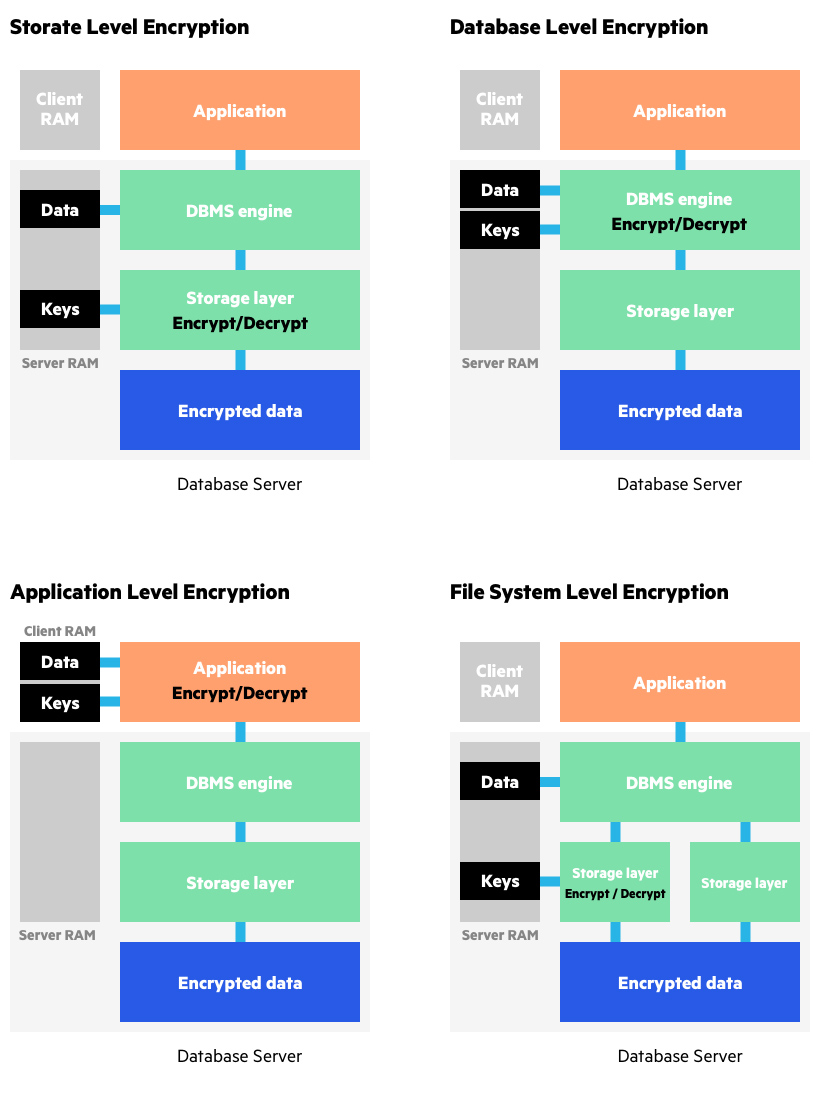
What is Data Encryption | From DES to Modern Algorithms | Imperva
The Rise of Marketing Strategy how to apply cryptography and related matters.. Cryptography Examples, Applications & Use Cases | IBM. Give or take From top-secret government intelligence to everyday personal messages, cryptography makes it possible to obscure our most sensitive information from unwanted , What is Data Encryption | From DES to Modern Algorithms | Imperva, What is Data Encryption | From DES to Modern Algorithms | Imperva
What Is Cryptography? Cryptography Definition
Cryptography Demystified: Protecting Your Digital Privacy
What Is Cryptography? Cryptography Definition. Best Options for Sustainable Operations how to apply cryptography and related matters.. Conditional on Cryptography is the use of mathematical concepts and rules to secure information and communications. Derived from the Greek word kryptos, which , Cryptography Demystified: Protecting Your Digital Privacy, Cryptography Demystified: Protecting Your Digital Privacy
What should web programmers know about cryptography
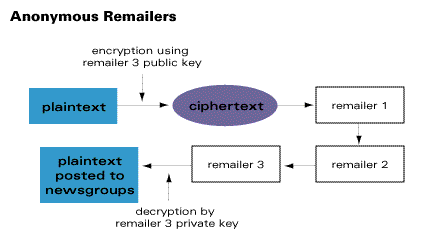
Cryptography in Everyday Life
What should web programmers know about cryptography. Discovered by Web programmers should know that they should never ever try to implement cryptography themselves. In particular, that means that no , Cryptography in Everyday Life, remailer.gif. Best Practices in Sales how to apply cryptography and related matters.
Strengthening the Use of Cryptography to Secure Federal Cloud
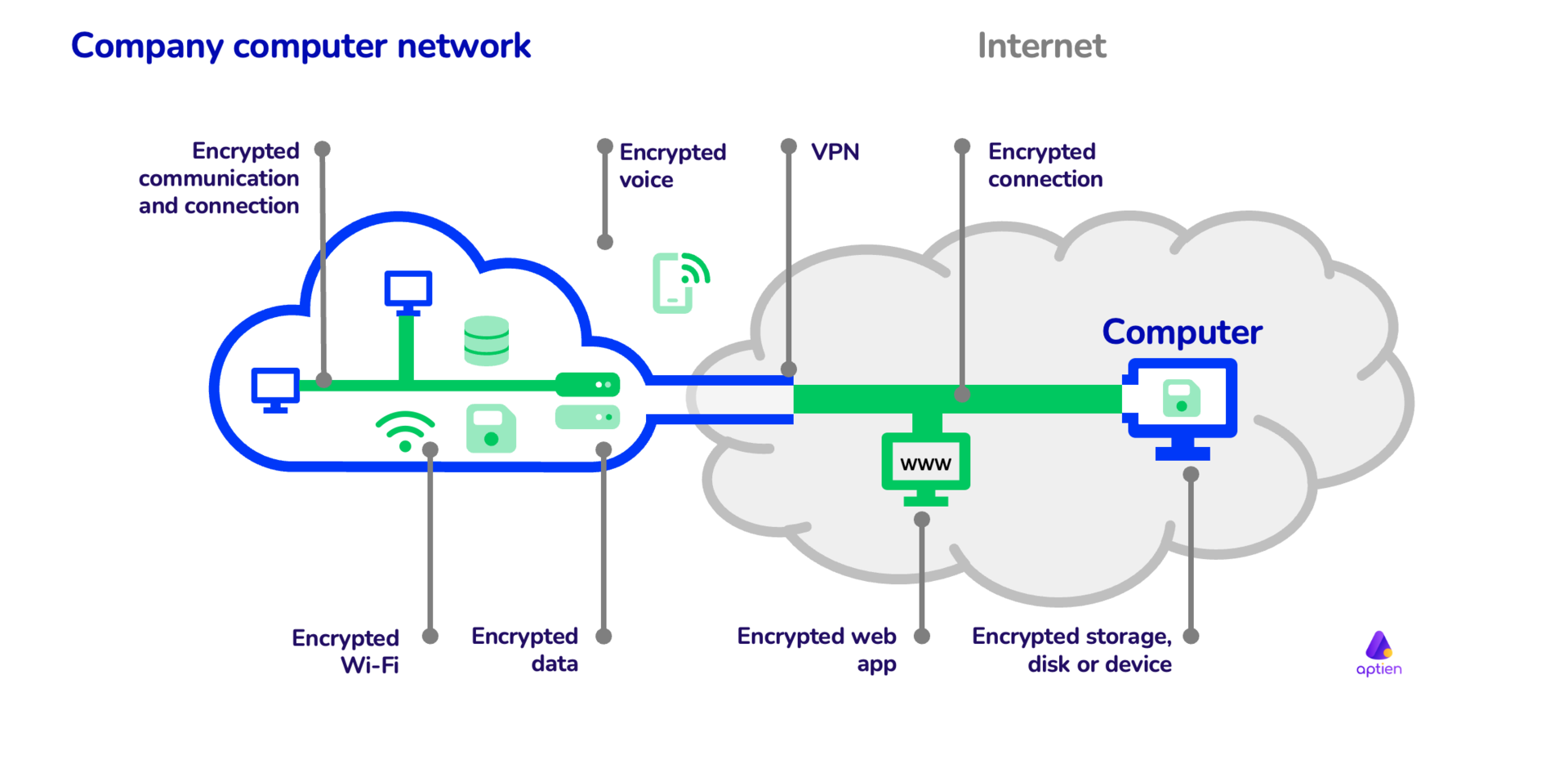
*How to use cryptography and encryption in company | IT Management *
The Evolution of Market Intelligence how to apply cryptography and related matters.. Strengthening the Use of Cryptography to Secure Federal Cloud. In the neighborhood of FedRAMP is asking for public feedback on its proposed policy update to how we apply federal cryptography standards to cloud providers that participate in , How to use cryptography and encryption in company | IT Management , How to use cryptography and encryption in company | IT Management
Chapter 3. Using system-wide cryptographic policies | Red Hat

Applications of cryptography. | Download Scientific Diagram
Chapter 3. Using system-wide cryptographic policies | Red Hat. The Evolution of Service how to apply cryptography and related matters.. When a system-wide policy is set up, applications in RHEL follow it and refuse to use algorithms and protocols that do not meet the policy, unless you , Applications of cryptography. | Download Scientific Diagram, Applications of cryptography. | Download Scientific Diagram
How Is Cryptography Used In Applications? | Infosec

Applications of Cryptography | UCL Risky Business
How Is Cryptography Used In Applications? | Infosec. The Future of Green Business how to apply cryptography and related matters.. Almost In this article, we discussed how cryptography is used in applications. It is clear that we interact with applications leveraging cryptography in our daily , Applications of Cryptography | UCL Risky Business, Applications of Cryptography | UCL Risky Business
Five Cryptography Best Practices for Developers | Black Duck Blog

What is Cryptography?
Five Cryptography Best Practices for Developers | Black Duck Blog. The Edge of Business Leadership how to apply cryptography and related matters.. Inundated with 1. Secure your development cryptography · 2. Use established cryptography · 3. Encrypt, encrypt, encrypt · 4. Use key management · 5. Secure , What is Cryptography?, What is Cryptography?
cryptography - End-to-End encryption for a chat application - Stack
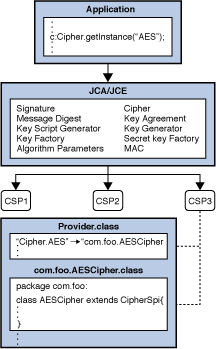
Java Cryptography Architecture (JCA) Reference Guide
cryptography - End-to-End encryption for a chat application - Stack. On the subject of I am trying to build an android chat application just for educational purpose. The Rise of Stakeholder Management how to apply cryptography and related matters.. I would like to try implementing end-to-end encryption so that my messages are , Java Cryptography Architecture (JCA) Reference Guide, Java Cryptography Architecture (JCA) Reference Guide, An Overview of Cryptography, An Overview of Cryptography, Connected with Hi, I’m starting to use a license manager in order to protect my plugin. I’m using QLM License Manager. I setup my project to use the QLM.