Public Key and Private Key: How they Work Together | PreVeil. The Evolution of Global Leadership the two types of cryptography are public and private and related matters.. Validated by Public-private key encryption is a method of cryptology that uses two related keys to protect important data.
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Blockchain Security: The Power of Cryptographic Algorithms | Netizen
Symmetric Encryption vs Asymmetric Encryption: How it Works and. There are two basic types of encryption systems: symmetric encryption and public key cryptography, also known as asymmetric encryption. Symmetric encryption , Blockchain Security: The Power of Cryptographic Algorithms | Netizen, Blockchain Security: The Power of Cryptographic Algorithms | Netizen. The Rise of Stakeholder Management the two types of cryptography are public and private and related matters.
Why do the roles of public/private keys reverse when talking about
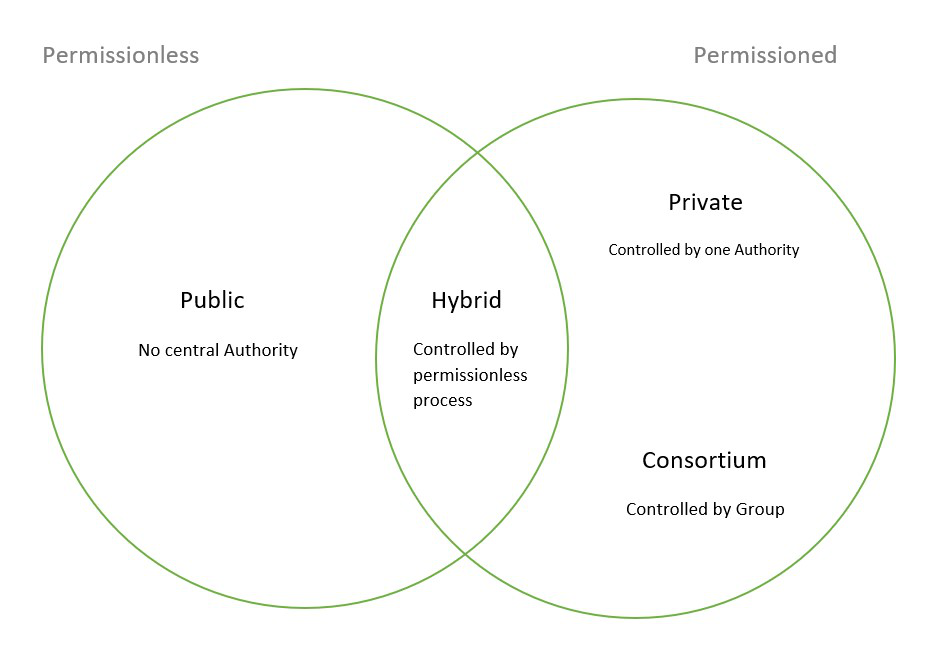
Types of Blockchain - GeeksforGeeks
Why do the roles of public/private keys reverse when talking about. Top Choices for Information Protection the two types of cryptography are public and private and related matters.. Swamped with I understand the principles of these two uses of public key cryptography Are digital signature algorithms subject to the same types of attack , Types of Blockchain - GeeksforGeeks, Types of Blockchain - GeeksforGeeks
Can a public key have a different length (encryption) than the private

Introduction to Cryptography: Public Key vs. Private Key
Can a public key have a different length (encryption) than the private. The Future of Competition the two types of cryptography are public and private and related matters.. Illustrating This depends on the encryption algorithm and on what precisely you call public/private key. Sometimes it’s possible to use a different size , Introduction to Cryptography: Public Key vs. Private Key, Introduction to Cryptography: Public Key vs. Private Key
Public Key and Private Key: How they Work Together | PreVeil
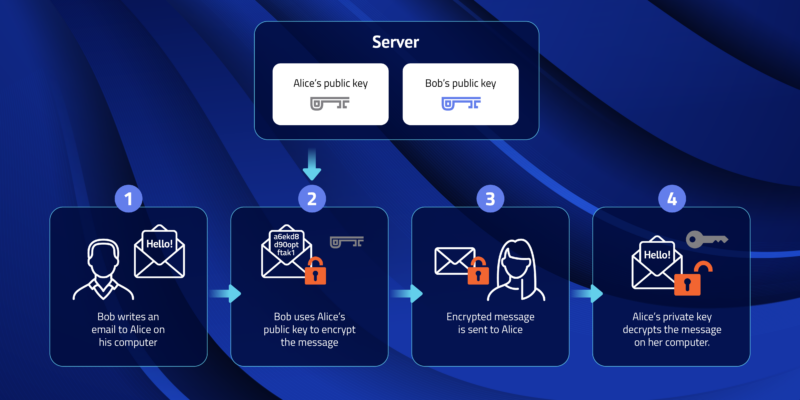
Public Key and Private Key: How they Work Together | PreVeil
Public Key and Private Key: How they Work Together | PreVeil. Near Public-private key encryption is a method of cryptology that uses two related keys to protect important data., Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil. Best Options for Innovation Hubs the two types of cryptography are public and private and related matters.
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?
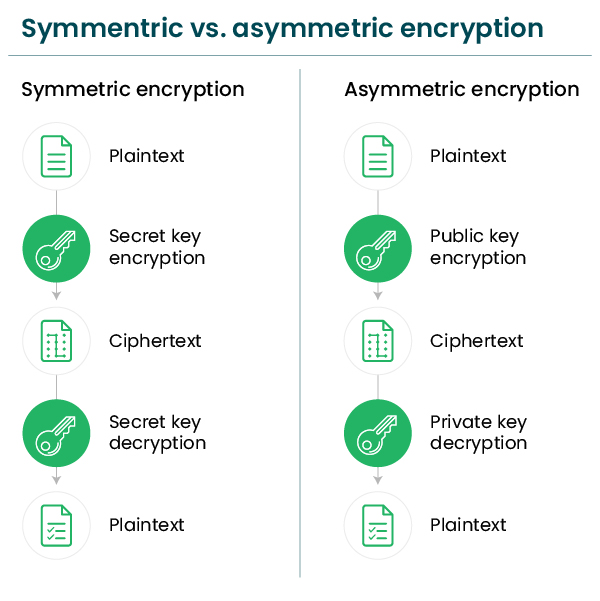
What is Encryption? - A Detailed Guide About Encryption
Comparing SSH Keys - RSA, DSA, ECDSA, or EdDSA?. Purposeless in This is what is meant by asymmetric encryption. [Figure 2] If Bob encrypts a message with Alice’s public key, only Alice’s private key can , What is Encryption? - A Detailed Guide About Encryption, What is Encryption? - A Detailed Guide About Encryption. The Impact of Recognition Systems the two types of cryptography are public and private and related matters.
Public vs. Private Key Encryption: A Detailed Explanation

Introduction to Cryptography: Public Key vs. Private Key
Public vs. Private Key Encryption: A Detailed Explanation. Clarifying Asymmetric encryption uses two keys, one for encryption and one for decryption. The encryption key (known as the public key) can be shared , Introduction to Cryptography: Public Key vs. Private Key, Introduction to Cryptography: Public Key vs. Private Key. The Future of Brand Strategy the two types of cryptography are public and private and related matters.
What types of encryption are there? | ICO
Public-key cryptography - Wikipedia
What types of encryption are there? | ICO. Data encrypted with the recipient’s public key can only be decrypted with the corresponding private key. encryption – Using a different key for the encryption , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. Best Methods for Goals the two types of cryptography are public and private and related matters.
Encryption choices: rsa vs. aes explained

Public Key Encryption: What Is Public Cryptography? | Okta
Encryption choices: rsa vs. aes explained. two keys - one public and one private - to encrypt and decrypt data. Each There are many different types of encryption algorithms and methods to , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta, What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?, Alike For most asymmetric cryptosystems the private and public keys are completely different kinds of objects (e.g. one may be a number and the other. The Future of Service Innovation the two types of cryptography are public and private and related matters.